GitOps -Terraform-Vault-Serverless
This article demonstrates using Git as the single source of truth to build an Infrastructure in aws using some of the best practices available.
Requirement at a Glance:
- Highly available web app , using the servless offering of aws
- Secure access of Credentials to build Infrastructure.
- Use terraform - with remote state management.
- Web App should reside in a Private Space
- Infra should be scalable to support multiple environments.
- Use conventional commits.
Solution Offering:
- Highly available web app , using the servless offering of aws : Use AWS lambda
- Secure access of Credentials to build Infrastructure: Use Hashicorp Vault to render dynamic aws credentials
- Use terraform - with remote state management : Use S3 to store state files.
- Web App should reside in a Private Space : Mount AWS lambda in a Private Subnet
- Infra should be scalable to support multiple environments: Expose variables that can create different environements , Use terraform modules for scaling components as well as for ease of readability
- Use conventional commits - Commits were used with the following prefix "feat , fit". This can be used to generate changelog. (TODO)
High Level Overview
(Click image to zoom)
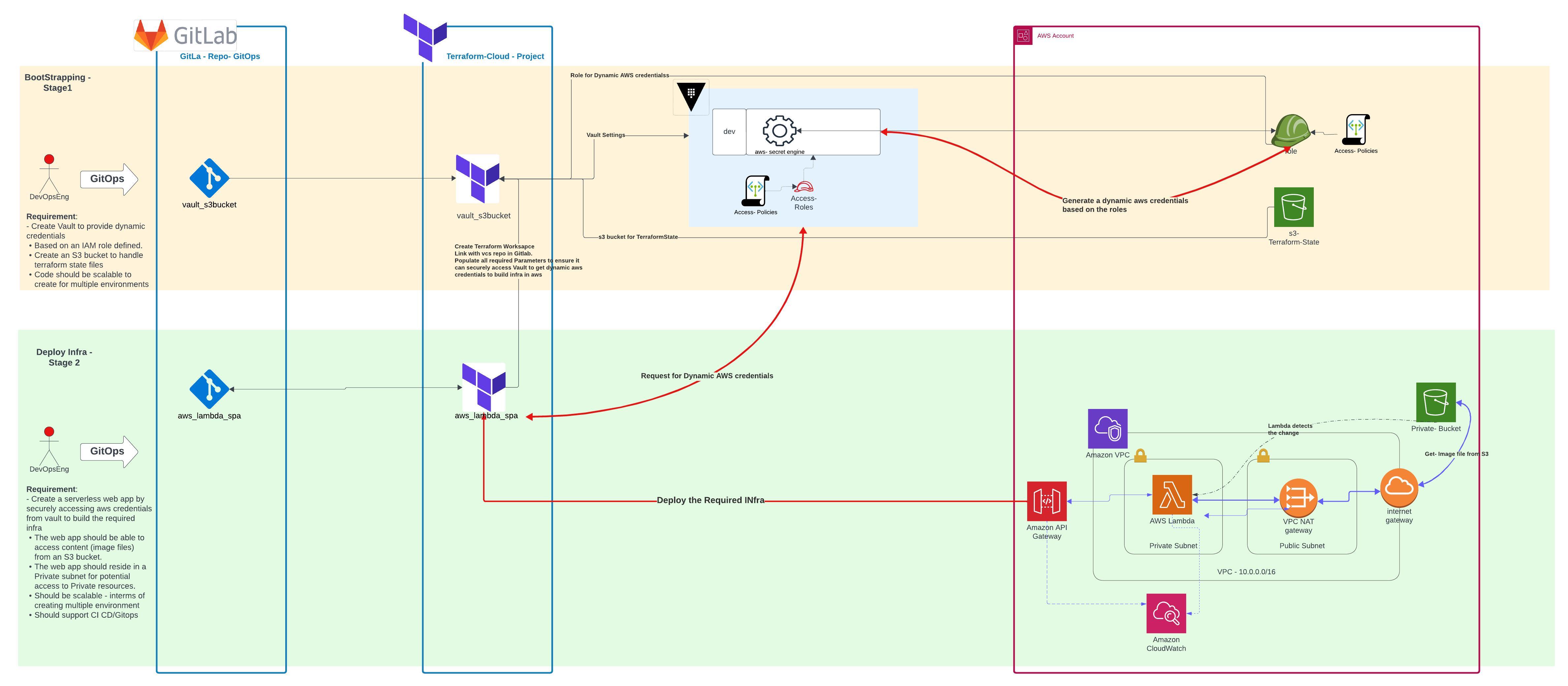
Bootstrapping
Repo link : https://gitlab.com/vineethbhargavan/terraform_vault_aws/vault_s3bucket.git
Implementation Notes:
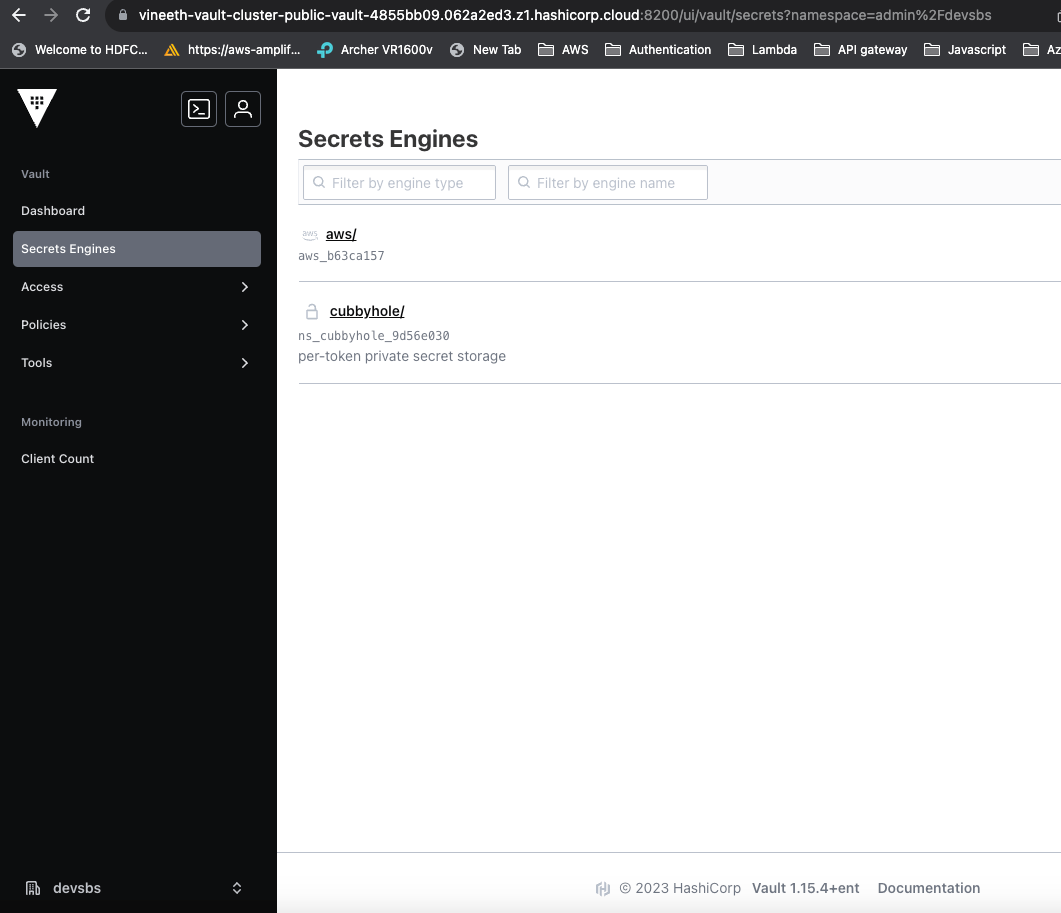
- Create Vault Namespace for a fixed environment (say "dev")
- The Namespace will have an aws secret engine which will associate with aws to provide dynamic credentials upon invoked.
- The Namespace will have polices and roles - which will make use of the auth type ,JWT to authenticate with Terraform cloud to provide dynamic aws credentials for terraform to build infrastructure in aws.
- Create AWS role and Policy - this will be used to map the access rights for the dynamic credentials generated by Vault during runtime (i.e when workspaces invoke vault)
- Create an S3 bucket to handle terraform state file.
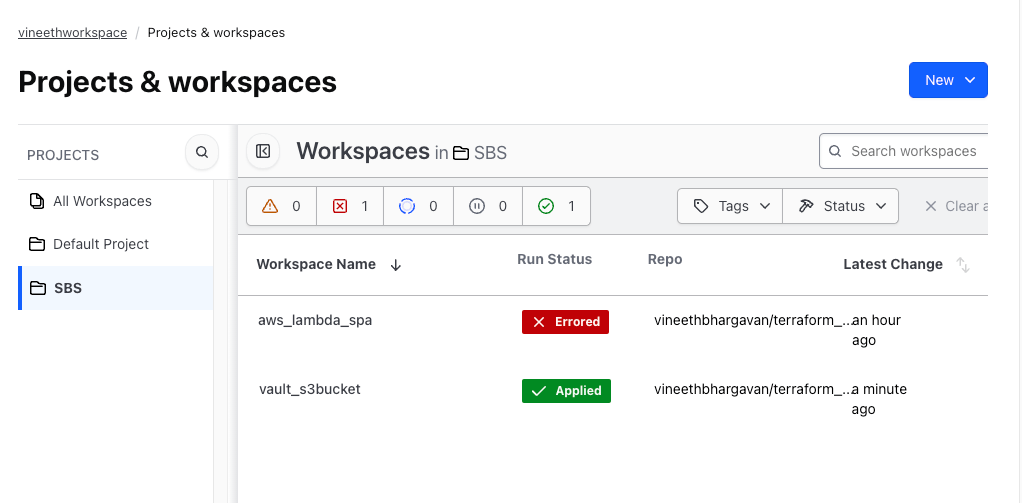
- Create a Terraform workspace with the required set of variables - to faciliate aws dynamic credential generation upon integrating with vault. The creation of terraform workspace is handled by the terraform code.
- All code block will have an variable named "environment" - which helps us to scale the entire infra (including vault namespace) for multiple environments.
Deploying WebApp
Repo link : https://gitlab.com/vineethbhargavan/terraform_vault_aws/aws_lambda_spa.git
Implementation Notes:
- All code block will have an variable named "environment" - which helps us to scale the entire infra for multiple environments.
- Loadbalancing and selfhealing are provided by virtue of having API Gateway and Lambda.
- Lambda is mounted in a VPC - Private Subnet.
- A private S3 bucket is used to zip the artifact of lambda function
- The same s3 bucket is used to store an Image file which will be used to render an Image in the HTML content.
Solution at a glance
URL : https://cgol2m0w55.execute-api.ap-southeast-2.amazonaws.com/devsbs_lambda_stage/hello
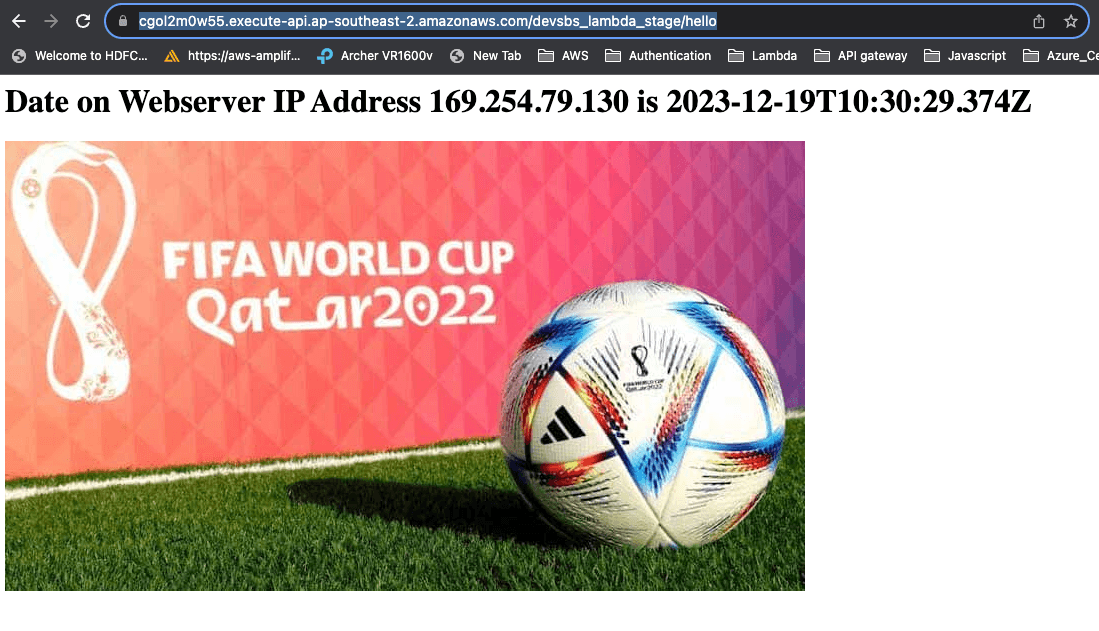
- "169.254.79.130" is part of the link-local address range. Specifically, it is within the Automatic Private IP Addressing (APIPA) range, which is reserved for self-assigned IP addresses when a device cannot obtain an IP address from a DHCP server. Need further exploring to figure out if an IP within the CIDR range of VPC can be derived from a lambda function.
Vault at a glance
Terraform Project Overview
Reference
- https://developer.hashicorp.com/terraform/tutorials/cloud/vault-backed-dynamic-credentials